ManySecured SIG Charter
1. Purpose of the ManySecured Special Interest Group
The ManySecured initiative is by the many (manufacturers and stakeholders in the ecosystem value/supply chain, etc.), for the many (users).
The ManySecured Special Interest Group (MS-SIG) has been established with the aim to better protect users (including consumers, businesses, industry and other enterprises) from the security risks posed by IoT devices. The primary methods of achieving this will be through innovation at the gateway and security collaboration with IoT stakeholders.
2. Status of this Charter
This Charter is written collaboratively by the MS-SIG to inform participants how we intend to operate and produce outcomes. The Charter is subservient to the ManySecured Legal Framework; for the avoidance of doubt, where there is conflict between this Charter and the Legal Framework, the Legal Framework takes precedence.
The Charter will be updated as required throughout the life of the MS-SIG. Any SIG Member may propose amendments and they will be discussed by the MS-SIG. Agreed proposals will be submitted to the MS-SIG Board for approval.
3. Scope and outputs of MS SIG
The MS-SIG is an enduring initiative to increase awareness of the vulnerability of IoT devices and how these can be mitigated at the gateway through the adoption of new standards, frameworks and threat-based collaboration services. The scope of the MS-SIG will be updated as the wider environment evolves and potential benefits are targeted.
The MS-SIG will seek to inform and to exploit the work being undertaken within the ManySecured Gateway Project (see below). The aims and outputs of the MS-SIG are to:
- Produce Best Practice recommendations in the areas of Gateway Foundations, Secure Comms, Update Management, Network Isolation
Develop and publish Problem Statements, Whitepapers, Requirements and Solutions
Define methods and algorithms to monitor, detect threats and suspicious activity in IoT devices and networks
Share datasets for:
- test purposes
- malware trace data
- fingerprints and patterns
- sample network traffic of vulnerable and compromised devices
Create reference (Open Source) implementation solutions
Develop a ManySecured Certification Program
Run trials with end users, customers and key stakeholders
The aims may be refined by the SIG Board as our understanding matures. To adhere with Competition Law, the requirements for outputs shall be based on objective criteria.
The MS-SIG is complementary to the ManySecured Project funded by Innovate UK (IUK). The IUK MS Project has a defined list of outputs which will be delivered under its own governance, schedule and budget. The relationship between the MS SIG and the Innovate UK MS Project is shown in Figure 1 below:
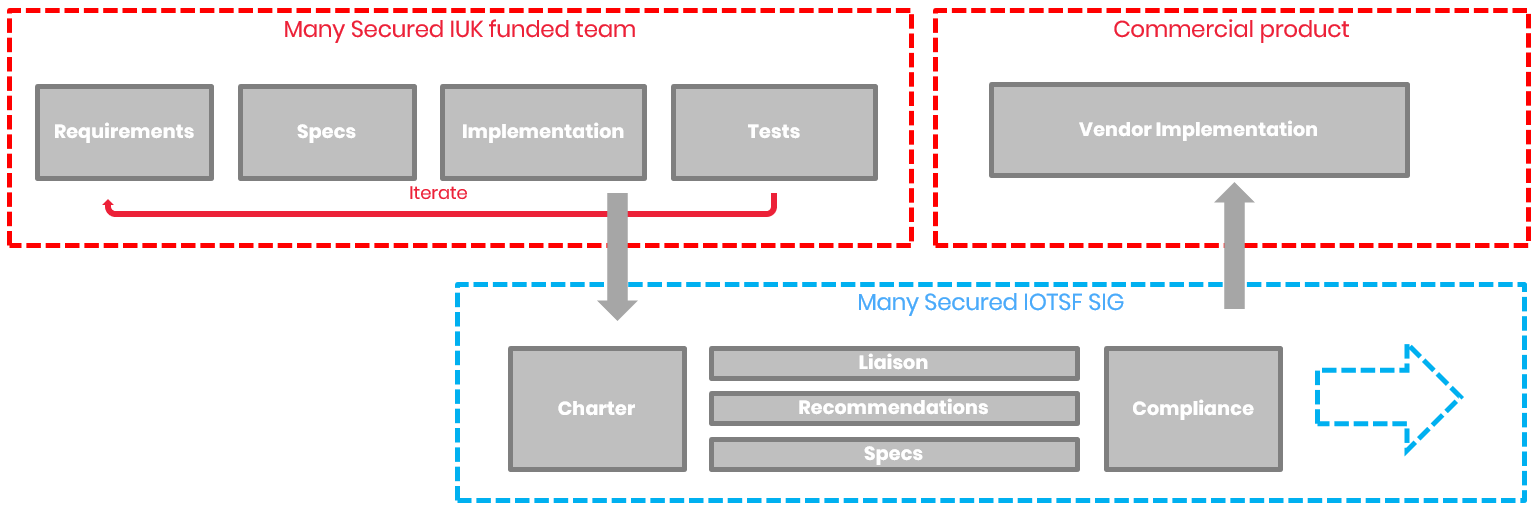
Figure 1: Relationship between the MS SIG and the Innovate UK MS Project
4. Principal areas of collaboration
The system of interest (SOI) spans the end-to-end system from the end point devices, gateways, manufacturers databases and drivers, and cloud-based analytics. The SOI includes legacy components and recognises that many IoT devices do not use IP as the networking technologies.
The areas of collaboration are:
- Foundations, including trust chains.
- Secure communications
- Updates
- Monitoring
- Network isolation
- Threat detection
- Smart control
- Threat sharing, including vulnerability disclosure
The MS SIG will generate Work-Streams (WSs) addressing specific topic areas as required. This Charter will apply to each WS, but the WSs can create its own sub-Charter to address specific areas that are not included in this Charter. The initial WSs include:
- Secure Usable Intranet Browser (SUIB)
- Distributed Device Descriptors (D3)
- Network Monitor (D3Events)
- Network Control (DCon)
- Gateway/Router Certification (GCERT)
5. Legal constitution
All SIG Work Group activities will take place under the ManySecured SIG Legal framework as set out in the ManySecured SIG Application Form and associated Annex. SIG Members are required to complete and sign this application form, copies of which are available on request using the contact form at: https://manysecured.net/contact
6. Governance and Organisation
Membership of the MS-SIG is open to organisations and individuals who have joined the IoTSF and have signed the ManySecured Legal Framework (when finalised).
The MS-SIG falls under the management and organisation of the IoTSF, which is a managed community within TechWorksHub Limited. The MS-SIG was initiated as an output from the Innovate UK funded MS Project.
The MS-SIG Co-Chairs are:
Nick Allott (NquiringMinds)
John Moor (IoTSF).
MS-SIG Co-Ordinator:
- Ian Poyner (IoTSF)
7. Internal communications
The MS-SIG shall fully comply with Competition Law and shall not not discuss prices, costs, marketing and sales activities, or business plans in adherence to Annex 3 of the Legal Framework.
- The MS-SIG will hold virtual meetings, typically every two weeks. Actions will be recorded in the Minutes of Meeting and their status will be reviewed at the start of each meeting.
- The main repository for project documents shall be GitHub (see Artefact control), with uncontrolled copies on Basecamp for information only.
- Specific issues and proposed edits regarding documents/artefacts should be raised as Issues or Actions in GitHub. For convenience, SIG-Members can raise issues and suggestions via Basecamp, and these will be transferred to GitHub issues and actions, if required, by the MS-SIG Co-Ordinator.
- Day-to-day messaging will be via Basecamp.
8. Stakeholders
To have a permanent impact, our outputs need to become embedded into the wider IoT ecosystem. To leverage our influence, we need to collaborate with stakeholders who have an interest in IoT security. Our stakeholders and audience include:
- UK Innovate
- IoTSF Plenary
- Standards bodies, such as IETF, W3C, NIST
- Trade bodies and alliances, such as Zigbee CHIP, FIDO Alliance
- Other security initiatives, such as OpenWRT.
- Government Agencies, Policy Makers and Regulatory Bodies
- Industry Consortia and Standards Bodies
- System Integrators
- Solution Vendors
- Application/Middleware/Security Software Vendors
- Security Software Vendors
- Device Management Software Vendors
- Cloud Platform Vendors
- Communication & Internet Service Providers
- Trusted Security Authorities
- Original Equipment Manufacturers (OEMs), Original Design Manufacturers (ODMs), Distributors and Value-Added Resellers
- Hardware/Chip Vendors
- Embedded Software Vendors
- IP Vendors
- Influencers
Stakeholder engagement will be co-ordinated through the IoTSF Co-Chair.
The ManySecured web-site is one of the channels intended to inform the wider community and public about our activities. Members are encouraged to submit articles for the web-site to the MS-SIG Co-Ordinator for review by the MS-SIG.
9. Artefact control
'Artefact' in this section includes all media, such as documents, code, diagrams, engineering models, presentations etc.
The primary repository for storage and version control of artefacts shall be GitHub - TechWorksHub ManySecured-WGs. Sub-repositories will be used for WS-specific artefacts, e.g.:
The [GITHUB Conventions](https://github.com/TechWorksHub/ManySecured-SUIB/blob/main/GITHUB Conventions.md) are to be used, including the use of Markdown.
Any SIG member may propose new artefacts or amendments to existing artefacts. These should normally be discussed within the SIG or WS and then raised as Issues or drafted as Pull Requests within GitHub. Members who are not able to do this may raise comments in Basecamp, which will then be added to GitHub by the Editor.
Each repository shall have an Editor or Editorial Team to review and, where appropriate, incorporate non-contentious changes (such as typos or clarifications). Major changes are to be proposed as branches within GitHub for commenting and for review prior to the next SIG/WS meeting. The proposed changes will be reviewed at the SIG meeting by viewing the differences in the GitHub artefact. Acceptance of changes should be by unanimous agreement of all participants where possible. Where unanimity is not achieved, there will be a further two-week review period where the Editor will seek to reconcile the different views, with assistance from the MS-SIG Co-Ordinator. At the end of the two-week reconciliation period the proposed changes shall be reviewed at the MS-SIG. If unanimous acceptance is not achieved then the Editor(s) shall recommend an outcome to the SIG Board. The SIG Board will make the final determination of the changes within two weeks.
As a courtesy to members who are unable to access the GitHub repository, copies of artefacts (usually in PDF format) will occasionally be copied across to the Basecamp document store. Note that this will only be done for major changes to artefacts once agreed by the SIG. The Basecamp store will lag behind the GitHub repository and should not be relied upon as controlled copies of artefacts.
Public release of artefacts
Any public release of an artefact shall be controlled using existing IoTSF processes. Document formatting shall be in accordance with IoTSF styling. The IoTSF reserves the right to edit any artefact prior to public release. This will normally be done in consultation with the SIG Editors.
10. Resources
The MS SIG operates on a voluntary basis in accordance with the Legal Framework.