D3 Scope and Entities
The D3 system comprises the following key physical entities
| Entity | Description |
|---|---|
| Internet | The global internet sitting on the public IP addressable range |
| Intranet | Private address space, sits behind the router |
| Router | The primary router sits between the internet and the intranet. Will provide internal and external routing |
| Endpoint device | A device sitting on the intranet and connected via the router to (potentially) both the public and private internet space |
| Network extender | A device on the intranet which extents the internal network, providing some subset of router capabilities |
| Protocol bridge | A device on the intranet which converts between one protocol or another (e.g. Zigbee, Zwave, LoRa) |
D3 Model
The D3 model has the following key components
D3 Claim
A D3 claim, is a JSON or JSON-LD statements, which has been signed.
A D3 claim is a verifiable credential https://www.w3.org/TR/vc-data-model/
As such each D3 claim has:
- id: a URI typically used to refer to the claim
- type: information related to the type of credential this is
- credentialSubject: the entity about which a claim is being made
- issuanceDate: date on which it was issued
- issuer: entity making the claim
- proof: typically provided by the issuer as a method to verify the claim is genuine
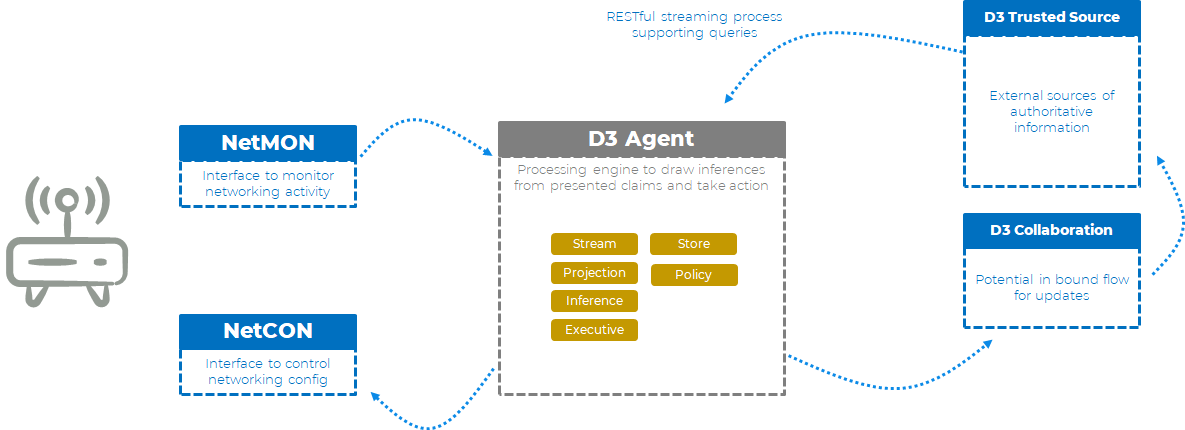
D3 Agent
A D3 Agent is any entity on the system which is capable of consuming D3 claims, processing these claims an making these claims and any derived claims available to upstream entities.
A D3 Agent may also be capability of initiating local (or remote actions).
In most of the scenarios discussed the primary D3 agent is the intelligent router, which is consuming events, making intelligent inferences and taking appropriate actions.
D3 Event Source
In the D3 model there can be one or more event sources. Event sources are streams of D3 statements.
These are real time claims, often made at speed and volume.
D3 events may not be explicitly signed. They may be issued as compressed data packaged on a stream which has been pre authenticated. Each event can be deem "implicit signed" by the entity that initiated and authenticated the stream.
D3 Event Source: D3Events
D3Events is a specific type of event stream that issues network events.
D3 Event Store: Memory
Each D3 agent may support the ability to recorded events in a memory store and make this available, for intelligent query.
D3 Authoritative sources
A D3 agent may have one or more authoritative sources, from which it receives information. An authoritative source will typically be an external cloud service, which the D3 agent trusts.
And authorities source, is technically identical to a D3 Event source, it is just typically remote.
Examples of authoritative sources are
- device type data bases
- device behaviour databases (e.g. MUD files)
- device vulnerability data bases (e.g. Mitre)
- threat intelligence databases (e.g. MISP)
D3 Processing Engine
The D3 processing engine, is a general purpose processing engine that is capable of drawing inferences from Event sources, creating new D3 claims derived from network events (meaningful insight) and triggering local actions.
The D3 processing engine is an implementation detail of the D3 Agent.
Concrete D3 example
To concretely implement a secure collaborative gateway, the following needs to be done
- D3 Event source: the primary event source is captured filtered network data. This is specifically modelled int he D3Events interface.
- D3 Actions: the preventative measures that the router is capability of is modelled in the DCon interface.
- D3 Event memory: event source memory will be implemented with a local instance of SQLlite
- D3 Authoritative sources: will be implemented using a basic HTTP RESTful interface to a single source of truth, hosted on IOTSF servers.
Standardisation scope
Within the ManySecured initiative we have the following items in scope
- Syntax and semantics of the primary D3 claims
- The functional interface for attaching to D3Events event source
- The functional interface for attaching to Event Memory
- The functional interface for attaching to DCon commands
- The functional interface for attaching to remote authoritative sources.
What is out of scope:
- The local inference engine is out of scope. It can be implemented many different ways
- The method by which an authorities source, prioritises or curates it D3 claims